7 min to read.
Abstract
When I look at Azure Built In Role Documentation I
always feel this is really big list of built in roles and hardly any Organization
will require to create new Azure custom role.
However when you work with Azure Customers, your faith
and beliefs are bound to fail. And if your customer is Bank, your concepts of Security
will fail.
So my customer started big on Azure Firewall. It was
maintained by their network administrators team. One fine day network admin
discovered that the Azure Firewall is visible to all users with Contributor and
Owner access.
Obviously the demand came that Owner/
Contributor should have full access EXCEPT Azure Firewall.
Damn Zero Trust!
Anyways, How to hide/ restrict Azure Firewall access
from Azure Owner and Contributors? Read on…
Have you heard of Azure custom roles?
The solution is simple. We need Custom Owner and Contributor
role that will have default access levels except for Azure Firewall.
Azure Built in Roles list is here - https://docs.microsoft.com/en-us/azure/role-based-access-control/built-in-roles.
If the Azure Built In Roles don’t meet the specific
needs of your organization, you can create your own custom roles.
So we will need to build custom Owner and Contributor
role that do not have access to Azure Firewall.
Always get Built in Role Definition first!
For simplicity I am going to build custom Contributor
Role only. Same can be replicated for Owner Role too.
First let us grab the built in role definition of
Contributor Role using Azure PowerShell.
If you do not have Azure PowerShell get it installed or
use it from Azure Shell. I want to edit the role definition on my local laptop
so I am using Azure PowerShell from my local machine.
First login to correct Azure Subscription and Azure AD.
I have seen major bomb blasts due to wrong selection of Subscription and Azure
AD Tenant.
Connect-AzAccount -Subscription YourSubscriptionID -Tenant YourAzureADTenantName-Like-Something.onmicrosoft.com
Get Contributor Role definition in JSON format with
below command –
Get-AzRoleDefinition -Name "Contributor" | ConvertTo-Json | Out-File "YourPath\Contributor.Json"
Make sure that correct Path is selected as per your
choice in above command. The Contributor role definition JSON will be created
at specified location and it looks similar to below screenshot. Open JSON in
Visual Studio Code. [click to get better view].
Modify the Contributor Role to Restrict Azure Firewall access!
I copy pasted above Contributor Role JSON to another
document in VS Code changed the name of file..
The name of the role I changed to “Contoso-Contributor.json”.
Now take quick steps as mentioned below –
1. Remove the Id filed completely. When you create role in Azure PowerShell; ID filed automatically gets created for you.
2. As this is going to be customer Azure Role; change “IsCustom” property to True.
3. Change the description that suits to your needs. I changed it to – Contoso Contributor Grants full access to manage all resources, but does not allow you to assign roles in Azure RBAC, manage assignments in Azure Blueprints, or share image galleries. However users with this role can't access Azure Firewall.
4. To remove the firewall access we need to add below line in NotActions segment of JSON as below – Microsoft.Network/azurefirewalls/*"
When we added * above, this means all types of actions are removed / restricted for Azure Firewall Resources. Make sure that you add “comma” on second last line.
5. Make sure you add the desired subscription at the bottom in “AssignableScopes” property. Unless subscription Id added the role will not be created. The format of subscription has to be as follows -
Refer to screenshot below – [click to get better view].
Create the Role Definition in Azure Subscription
Now run below PowerShell command to get the role created.
Make sure you use the Path of your choice where Contoso contributor json definition
is present.
New-AzRoleDefinition -InputFile "YourPath\Contoso-Contributor-NoFirewallAccess.json"
The output of the command will be shown as below – [click
to get better view]
Assign the role to user
I have created a user named as Contoso User in My Azure
AD as shown below – [Click to get better view]
Then go to Azure Subscription -> Subscription ->
Select Subscription [which is used in AssignableScope] -> Access Control
-> Add -> Role Assignment. Selected Contoso User and assigned custom
contributor role – [click to get better view]
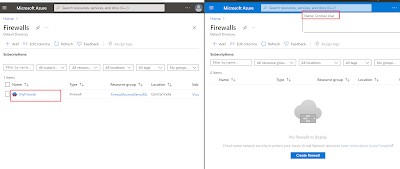
Verify Azure Firewall Access
So, I selected two users – One with Contributor role and
other with Contoso-Contributor Role. When click on Azure Firewall; I can
clearly see that even If the Contoso User has all the access same as normal
Contributor; the Azure Firewall Resource is not visible – [click to get better
view].
Conclusion
Hope this article helped to Custom Contributor role to
restrict / hide Azure Firewall.
Happy access control!!
A humble request!
Internet is creating a lot of digital garbage. If you
feel this a quality blog and someone will definitely get benefited, don't
hesitate to hit share button present below. Your one share will save many
precious hours of a developer. Thank you.
Next
Related Posts
4VNETs and transitive Routing using Azure firewall
Azure
Virtual Machines – real world frequently asked questions – not easily answered.
Azure
Migration frequently asked questions, not easily answered!
Azure
VM disk encryption, what should be my approach!





Hi, I did a similar custom role as your example, it works as expected with Firewalls, VNETs etc, but I was surprised that it does not suppress "Firewalls and virtual networks" in Storage account (as an example). I think it is because Azure is using a different REST endpoint Microsoft/Storage/Actions instead of the ones that we put into the NotAction. Any idea how you would enforce this? Thanks.
ReplyDelete