11 min to read.
Abstract
Corona Virus is giving birth to new technologies and new
way of working!
Remote work has been in the center of technology
discussion in all organizations. Azure Windows Virtual Desktop has been on
leading front to enable organization to enable remote working.
When we talk to security teams about remote working
using Azure WVD; every organization wants remote working incoming
traffic to flow through their perimeter firewall deployed on Azure. This is obvious
because all incoming traffic will be coming from internet and getting into
Azure WVD environment of customer.
This is fair ask and every organizations security team wants
to monitor all incoming traffic from internet.
So obvious question that comes to Azure Architects is -
Can you please make sure that all incoming/
inbound/ ingress traffic from client devices to Azure WVD flows through our
Firewall devices hosted on Azure?
The answer is Yes.
However in my opinion the question is incorrect!
How? Let’s talk about it.
Azure WVD and Reverse Connect
See, I am not blaming security team for asking incorrect
question; it is more of unawareness of how Azure WVD connection work. It is more
of responsibility of Azure Architects working within an organization to make
Security teams aware of how Azure WVD traffic flow and connections work.
Reverse connect is
a unique technology offered only on Azure WVD. Reverse connect technology means
your WVD host VM doesn’t need any inbound ports to be opened. Even the default
RDP port, TCP/3389, doesn’t have to be open. Instead, an agent creates an
outbound connection using TCP/443 into the Windows Virtual Desktop management service.
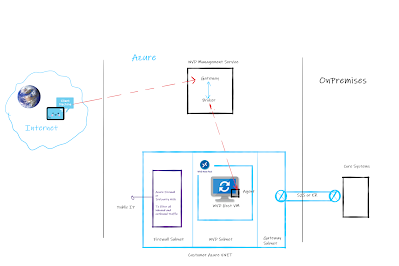
Most of the time we
misunderstand the Azure WVD Reverse Connect as shown in the Red color line in below diagram [click to get better
view] -
As per general understanding I have observed below
understanding of the traffic flow –
1. Client
device connects to WVD common URL either from browser or from app installed on
client machine. This traffic flows over internet.
2. The
request from client machine is forwarded to WVD management control plane.
3. The
broker in WVD management service initiates connection to actual WVD host. This traffic
also flows over internet.
In above traffic flow the traffic is reaching
to WVD host VM directly without passing through the firewall device.
This is not correct understanding.
Reverse connect means Broker will not initiate the traffic
to WVD host VM rather WVD host VM will initiate the connection to Broker of WVD
management service.
This means the traffic to connect to WVD
host is OUTBOUND/ EGRESS/ OUTGOING traffic from WVD host and not INCOMING/
INBOUND/ INGRESS traffic to WVD host VM.
Passing WVD host connection traffic through Firewall
Now that we understand about WVD host making outbound
call for honoring connection requests; we just need to have this traffic going
through Firewall device. The firewall device can be either NVA or Azure
Firewall.
To pass this outbound traffic initiated from WVD host VM
through firewall we will need to add UDR – User Defined Route on WVD Subnet.
The routes will be as follows –
-
If destination is on-premises then next hop
is Gateway
-
If destination is 0.0.0.0/0 then next hop is
firewall device private IP
The connection traffic will be falling under the
category of 0.0.0.0/0. This way connection traffic initiated from WVD host VM
will also pass through Firewall device.
This way security teams requirements will also be satisfied
as now they actually can inspect outgoing traffic in firewall from WVD Subnet.
Refer to below diagram – [click to get better view]
The correct network traffic flow will be as follows shown
in green in diagram –
1. Client
device connects to WVD common URL either from browser or from app installed on
client machine. This traffic flows over internet.
2. The
request from client machine is forwarded to WVD management control plane.
3. The
WVD host VM has an agent running on top of it. This agent then initiates the
traffic to WVD management service as an OUTBOUND connection.
4. WVD
management service traffic falls under category of 0.0.0.0/0 and hence the
traffic is forwarded to firewall device.
5. From
firewall device the traffic goes to WVD management service.
6. After
successful authentication from user the actual connectivity is established
between client device and WVD host VM.
All of this communication happens over 443 and there is
no requirement of opening 3389 default RDP port anywhere. This is the beauty of
WVD reverse connect.
Wrapping up
Remember, there is no Inbound traffic in
case of connecting to WVD host VM.
Therefore correct question to security teams –
Can you allow WVD connection traffic to pass through my
firewall device?
Answer - Yes using UDR on WVD subnet; we can pass WVD
connection traffic to flow from firewall device.
Conclusion
Hope this article helped to design your WVD deployment
architecture in right way and gave better understanding of WVD traffic flow.
Happy Remote working!!
A humble request!
Internet is creating a lot of digital garbage. If you
feel this a quality blog and someone will definitely get benefited, don't
hesitate to hit share button present below. Your one share will save many
precious hours of a developer. Thank you.
Next
Related Posts
Azure
Virtual Machines – real world frequently asked questions – not easily answered.
Start
stop multiple Azure VMs on schedule and save cost!
Azure
Migration frequently asked questions, not easily answered!

Its really great article
ReplyDelete